? The crypto industry is once again in the spotlight due to a bold hack: hackers stole approximately $1.3 million in cryptocurrency from the personal wallet of John-Paul Torbjørnsen, founder of the decentralized protocol THORChain.

Initial reports and protocol confusion
Immediately after the news, many analysts assumed that THORChain itself had been critically hacked. However, the project team quickly denied the rumors: “The incident is related to an attack on a user’s personal wallet and is not associated with THORChain’s security,” the network representatives emphasized.
Trust in the protocol remained, but questions about the founder’s personal cybersecurity remain.
How it happened: phishing and deepfake
Later, on-chain researcher ZachXBT revealed the details. According to him, the attack was carefully planned and executed via social engineering.
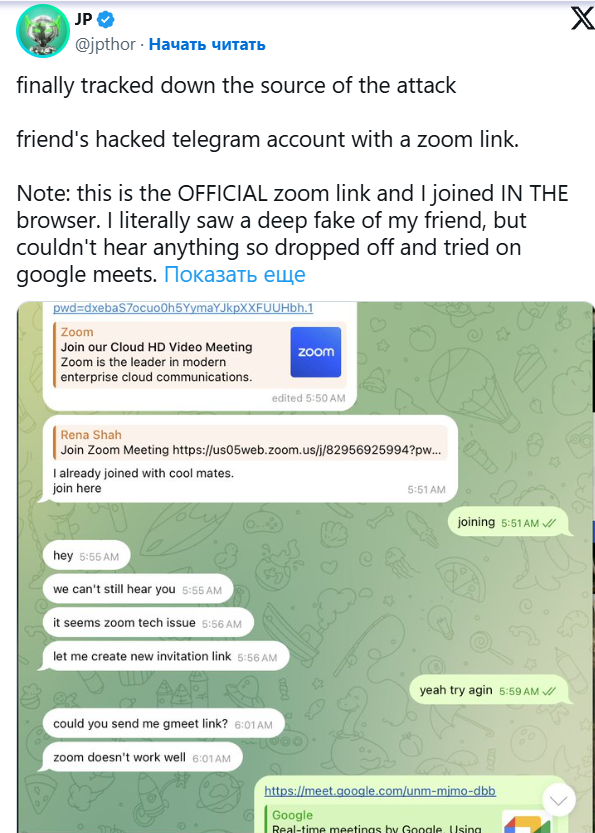
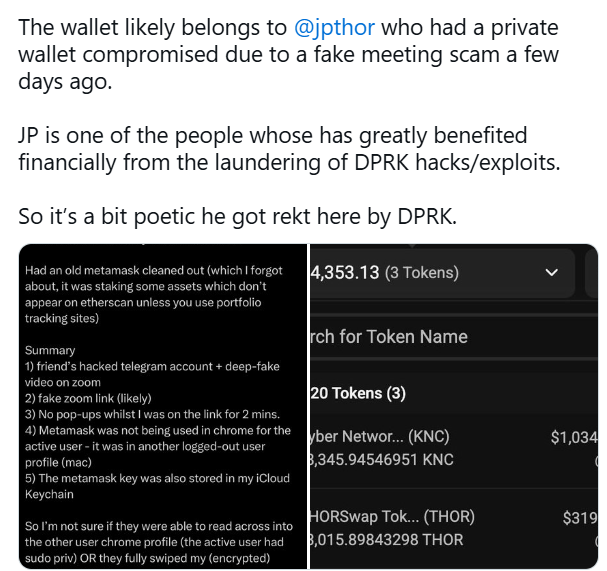
- On September 4, Torbjørnsen received a link to a Zoom meeting via Telegram. The message came from an account of his acquaintance that had previously been compromised.
- Upon clicking the link, he was confronted with a deepfake of his friend — the attackers used image and voice substitution technology.
- During a brief conversation (about 2 minutes), the criminals installed a malicious script on his computer, giving them access to private keys and wallet contents.
Assets totaling approximately $1.3 million were quickly moved between addresses.
North Korean trace and “poetic justice”
ZachXBT stated that North Korean hacker groups, known for cryptocurrency laundering operations — particularly the notorious Lazarus Group — are likely behind the attack.

“Torbjørnsen himself once profited from links to laundering funds obtained by North Korea from hacks and exploits. So it’s rather poetic that North Korea has now caught up with him,” the researcher remarked.
Response and attempts to recover funds
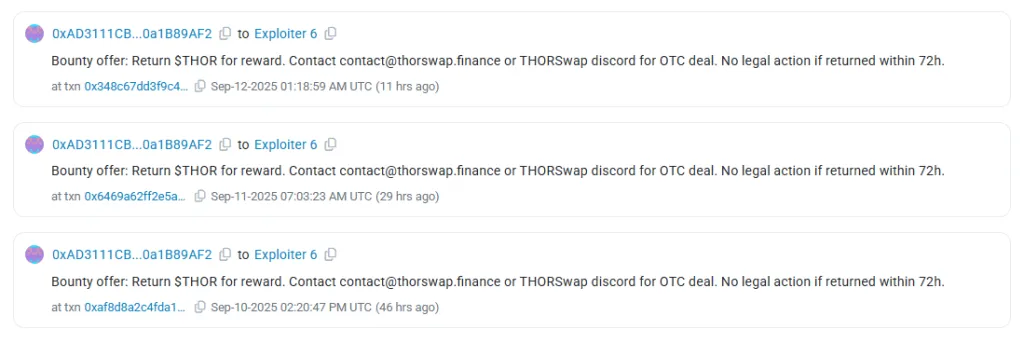
On September 12, the THORChain team sent on-chain messages to the attackers’ addresses, offering a reward for returning the stolen funds — a so-called “white-hat offer.” So far, no signs of willingness to return the assets have been observed.
Context: crypto hacks in 2025
The incident involving Torbjørnsen is part of a broader issue. According to PeckShield, in August 2025 alone, losses from attacks in the crypto industry exceeded $163 million. At least 16 major incidents were recorded, including direct protocol hacks and phishing campaigns using new technologies like deepfakes.

How to protect yourself: tips for crypto investors
This case demonstrates that even industry leaders are vulnerable to social attacks. To minimize risks, experts recommend:
- Never click on links from messengers without additional verification, even if they come from a known contact.
- Use a separate “clean” computer for storing crypto assets and performing transactions.
- Use hardware wallets and avoid keeping large sums in hot wallets.
- Verify meeting participants via another communication channel.
- Stay updated on new attack types — deepfakes are becoming increasingly convincing and will be used more frequently.
? Conclusion
This incident clearly shows that in the crypto world, the main vulnerability is not only protocol code but also people themselves. Whereas threats previously mainly came from hackers exploiting smart contracts, the focus is now shifting to personal attacks using the latest technologies.
By the way, you can get legendary hardware wallets for beginners here, with all the basic features included!
All content provided on this website (https://wildinwest.com/) -including attachments, links, or referenced materials — is for informative and entertainment purposes only and should not be considered as financial advice. Third-party materials remain the property of their respective owners.


