A mega trojan disguised as pirated games infected hundreds of thousands of computers: Far Cry and FIFA cracks turned out to be a trap
Fans of “free” games have received yet another reminder that piracy is not only about saving money – it is also about the risk of waking up one day without passwords, a crypto wallet, and personal data. Cybersecurity experts have uncovered a massive campaign infecting Windows computers through pirated copies of popular video games. The malware in question is RenEngine loader (or ReEngine), which may have already compromised more than 400,000 PCs worldwide.
The danger lies in the fact that the trojan is not spreading through suspicious emails or banner ads, but under the most familiar disguise for gamers – cracks and “hacked” versions of famous titles. The virus was discovered by researchers at Cyderes, who reported that infected installers were distributed together with pirated versions of Far Cry, FIFA, Need for Speed, Assassin’s Creed, and other well-known games.
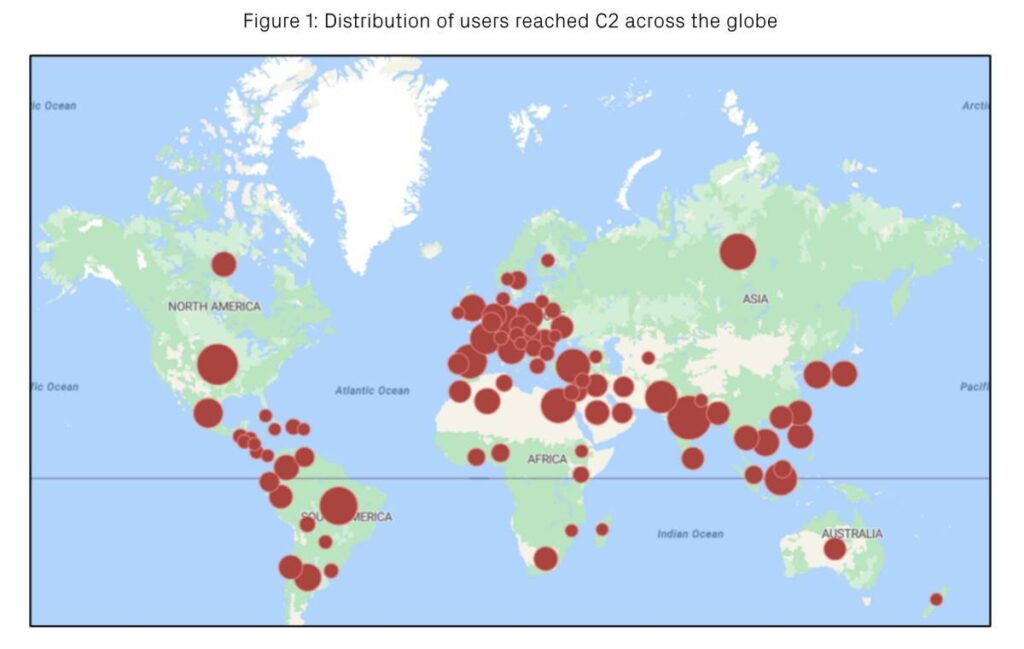
RenEngine spread geography. Image source: cyderes.com
The scheme works in the simplest way possible – and that is exactly why it is so effective. A user downloads a “repack,” launches the installer, sees a familiar interface, and starts playing without realizing that a malicious loader has already entered their system along with the game. RenEngine embeds itself into a legitimate Ren’Py-based game installer, making it particularly deceptive: the installation process looks normal, and the game actually runs. This is what allows the malware to remain unnoticed – the user gets what they wanted, so they do not suspect anything.
According to researchers, the malware has been active since at least April 2025 and continues to spread aggressively. Moreover, in October it received a major update: developers added a telemetry module that contacts the same address every time the infected program is launched. Thanks to this, specialists were able to estimate the scale of the outbreak – hundreds of thousands of machines have been infected so far.
Every day, RenEngine registers between 4,000 and 10,000 new victims. This means the campaign is not slowing down – on the contrary, it continues to gain momentum. The highest concentration of infections has been recorded in India, the United States, and Brazil, but Russia has also entered the top five countries by number of affected systems. Estimates suggest that more than 20,000 Russian computers may already be under the trojan’s control.
The main threat of RenEngine is that it is not just malware for malware’s sake. Its primary purpose is to secretly install data-stealing programs on the victim’s computer. First and foremost, it attempts to deploy ARC Stealer – a specialized infostealer that collects virtually everything of value to attackers.
This includes saved browser passwords, cookies, autofill data, login history, system information, clipboard contents, and even cryptocurrency wallets. In other words, if crypto exchanges were ever accessed, seed phrases stored, or banking data entered on an infected PC, all of that information may already have been stolen.
And that is not the limit. RenEngine loader has also delivered other malicious payloads, including Rhadamanthys, Async RAT, and Xworm. These programs not only steal data but also provide remote access, effectively turning the computer into a full-scale “zombie” controlled by hackers. In such cases, users may not even realize their PC is being used for further attacks or as storage for stolen information.
What is especially alarming is that most popular antivirus solutions show little reaction to RenEngine in the early stages of infection. According to Cyderes, only Avast, AVG, and Cynet currently detect the threat reliably. In many cases, the malware manages to establish itself in the system before standard security tools can recognize it.
Experts recommend that anyone suspecting infection should not rely on a simple “quick scan,” but instead use Windows recovery tools or, in extreme cases, completely reinstall the operating system. Infostealers are not the type of malware you can simply remove and forget – if data has already been stolen, consequences may surface weeks or even months later.
The RenEngine story is yet another example of how dangerous the pirated content market has become. Today, a “free game” may cost far more than a licensed copy: lost accounts, stolen funds, leaked personal information, and total loss of control over your computer.
So if you know someone who likes to download Far Cry with a “100% discount,” it might be time to send them this news. Because a mega trojan hidden in a crack is one case where the game can truly end very badly.
All content provided on this website (https://wildinwest.com/) -including attachments, links, or referenced materials — is for informative and entertainment purposes only and should not be considered as financial advice. Third-party materials remain the property of their respective owners.