Another reminder: in crypto, the most vulnerable part of the system is not the smart contract or the blockchain — it’s the human.
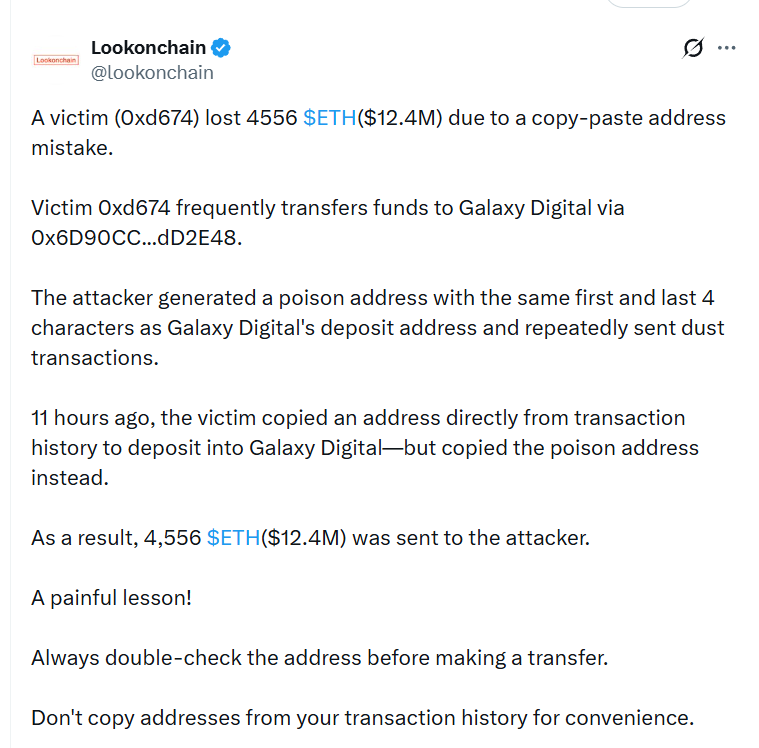
A user lost 4,556 ETH (about $12.4 million) while trying to deposit funds to Galaxy Digital. Instead, the money went to a scammer’s address. The cause: a classic address poisoning attack triggered by copying details from transaction history.
Technically, nothing was hacked. No exploits, phishing sites, or malware. Just plain haste and automatic behavior.
What actually happened
The user wanted to deposit to Galaxy Digital and opened their wallet or blockchain explorer transaction history. There, they saw a familiar-looking address — the same format, the same first and last characters. They copied it and sent funds.
Victim address: https://etherscan.io/address/0xd6741220a947941bf290799811fcdcea8ae4a7da
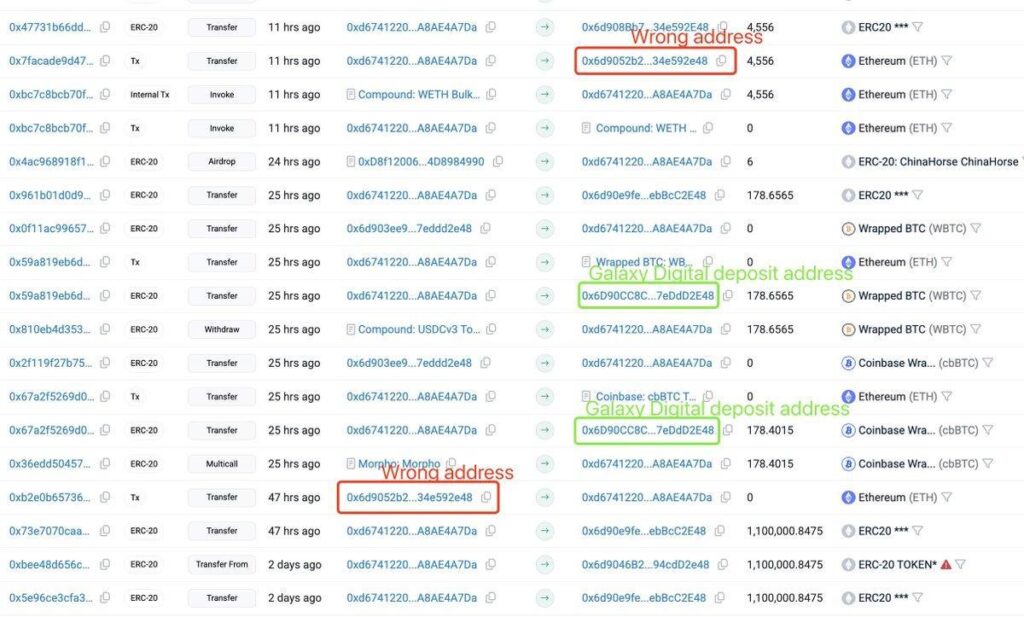
The problem: it was not Galaxy’s address, but a pre-prepared hacker address. The scammer had previously sent a zero-value (or “dust”) transaction so that their address appeared in the transaction history. At the right moment, the victim just copied the wrong address. The result: an irreversible transfer to the attacker’s wallet.
How Address Poisoning works
This scheme is as old as blockchain but still collects millions.
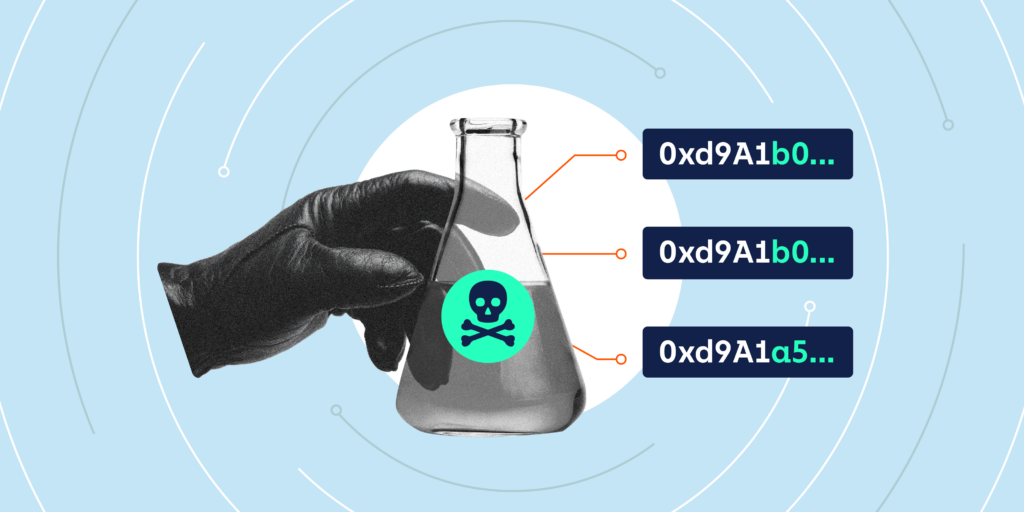
1. Generating a visually similar address
Scammers use software that generates millions of addresses until one matches the target’s first and last 4–6 characters.
Example:
0xA3F1…9C2E
0xA3F1…9C2E
The middle is completely different, but the brain ignores it.
2. Polluting transaction history
The hacker sends a zero-value transaction or minimal ETH to the victim. The money doesn’t matter — what matters is the address appearing in history.
3. Setting the trap
The scammer’s address becomes “recently active” or just noticeable in the transaction list. To the human eye, it looks familiar and “already used.”
4. Critical moment
The victim opens history to copy the address for transfer. In haste, they check only the start and end and hit Copy-Paste.
5. Irreversibility
The transaction goes to the blockchain. No cancellation. Support cannot help. The mistake costs millions.
Why it works: psychology, not cryptography
The human brain does not read long strings fully. It recognizes patterns. An address like “0x1234…ABCD” feels familiar if the start and end match. Most people ignore the middle. Scammers know this and forge the parts people actually see. It’s not a bug — it’s exploiting perception.

Why these mistakes are getting more expensive
Previously, such attacks cost users $5,000–50,000. Now — tens of millions.
Reasons:
- larger transaction sizes;
- institutional transfers;
- habit of working quickly;
- illusion of “I’ve done this a thousand times.”
The more experienced the user, the more dangerous the automation.
How to protect yourself
Never copy addresses from transaction history. Incoming or outgoing — never.
Use a whitelist/address book. For exchanges, custodians, funds, or frequent counterparties.
Check more than start and end. At least 3–4 characters in the middle.
Test transaction is mandatory. Send a minimal amount first for large transfers. Always.
QR codes > Copy-Paste. Use them if supported.
Conclusion
Address poisoning is not a “clever hack.” It’s an attack on attention and habit. Blockchain does not forgive small mistakes. Copy-Paste in crypto is high-risk. This time, the mistake cost 4,556 ETH. Next time, it could be yours.
All content provided on this website (https://wildinwest.com/) -including attachments, links, or referenced materials — is for informative and entertainment purposes only and should not be considered as financial advice. Third-party materials remain the property of their respective owners.


