The story of the “Apple hack” is in fact far more interesting and troubling than it appears in the headlines. Formally, it was not Apple itself that was attacked, but Luxshare – one of the key contract manufacturers and assemblers through which iPhones, AirPods, Apple Watch, Vision Pro, and other devices pass. But in modern electronics, this is almost the same thing. If you control the factory, the servers, and the internal documentation of the assembler, you effectively gain access to the nervous system of the entire supply chain.
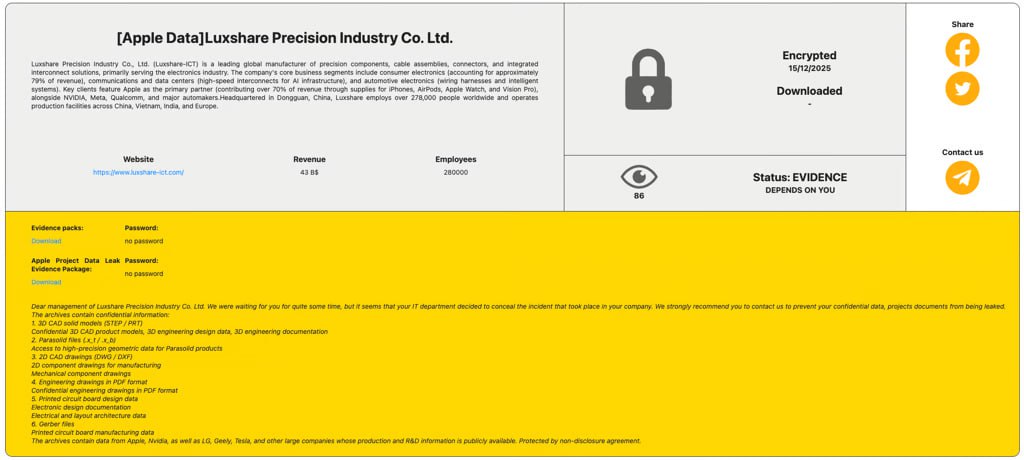
The hacking group RansomHub claimed responsibility for breaching Luxshare’s servers and says it stole around 1 terabyte of data. This is not about emails or accounting records, but about the most sensitive asset of any technology giant: 3D models of enclosures, circuit board schematics, manufacturing instructions, component specifications, and internal engineering documentation. Essentially, this is a complete “anatomical atlas” of devices – from the shape of screws to the routing of traces on circuit boards.

What makes this especially troubling is the claim that the archives contain data not only on current models, but also on devices that have not yet been announced. If this is true, the grey market is not getting a simple leak, but a ready-made manual for copying hardware before its official release. For China and the global counterfeit market, this is a gold mine. When you have exact dimensions, materials, layouts, and assembly logic, a copy does not appear a year after launch, but almost simultaneously with the product presentation.
An important point is that Luxshare does not work only with Apple. The list of allegedly stolen data also includes Nvidia, Tesla, LG, and Geely. This means the blow was not dealt to a single brand, but to an entire cluster of high-tech manufacturing. If the leak is confirmed even partially, it will become one of the largest compromises of production information in recent years. And the most unpleasant aspect for companies is that such data cannot be “revoked” or quickly replaced like a password. Circuit designs and structural solutions do not change in a week.
The attack model here is illustrative. For decades, Apple has built a reputation as a company obsessed with secrecy. Closed presentations, NDAs, separate floors for different teams, leak control bordering on paranoia. But this entire system fails at exactly one point – where real production begins. The more complex the device and the more global the supply chain, the more contractors, factories, and servers exist that are physically outside Apple’s direct control. And that is precisely where hackers are increasingly striking.
If RansomHub does indeed publish or sell the data, the consequences will be multi-layered. For Apple, this is less a reputational blow than a strategic one. The grey market will be able to release externally identical devices faster and cheaper. Competitors will gain hints about engineering solutions. And the leak economy will once again be reminded that secrecy in the era of distributed manufacturing is more an illusion than a reality.
This leads to an almost philosophical point. Even if the leak turns out to be catastrophic, it is unlikely to radically change anything for the average user. Visually, future iPhones have long ceased to be a surprise. The irony is that the question “What will the iPhone 20 look like?” increasingly receives an honest and boring answer: roughly the same as the iPhone 17. Flat edges, glass, minimal changes, cosmetic tweaks. The real differences have long moved inside – into chips, cameras, energy efficiency, and the ecosystem.
Therefore, the main risk of this story is not that someone might see the design ahead of time. The main risk is that breaches of contractors are becoming a systemic threat to the entire industry. This is a new reality in which companies must protect not only their own servers, but also dozens of partners around the world. And the further this goes, the clearer it becomes: the weakest link in the chain determines the security of the entire brand, no matter how expensive or iconic it may be.
All content provided on this website (https://wildinwest.com/) -including attachments, links, or referenced materials — is for informative and entertainment purposes only and should not be considered as financial advice. Third-party materials remain the property of their respective owners.