SlowMist has identified a new phishing attack targeting users of the MetaMask crypto wallet. As part of the scheme, attackers impersonate the project’s security service and use fake “two-factor verification” (2FA) to trick users into entering their seed phrases themselves. Although 2FA is usually associated with enhanced security, in this case the term is used solely as a social engineering tool.
According to SlowMist experts, the scheme consists of several stages, each carefully designed to avoid raising suspicion among unprepared users.
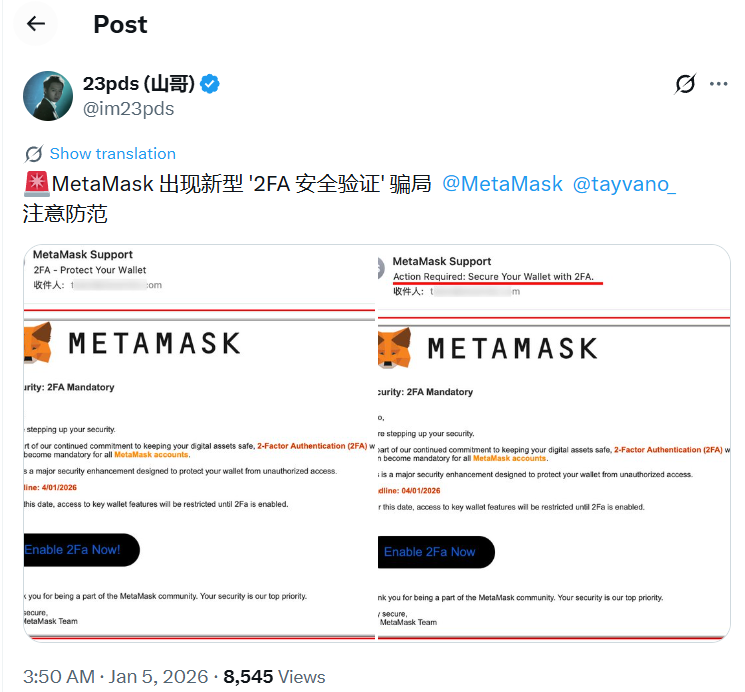
Users receive emails or notifications allegedly sent on behalf of MetaMask, claiming there is an urgent need to complete a security check or update protection settings. Visually, these messages and websites look highly convincing: they use official branding, the fox logo, and correct terminology. To increase credibility, scammers register domains that are almost indistinguishable from the official ones – sometimes differing by just a single letter, which is easy to miss at a glance.
After clicking the link, users are guided through a “security enhancement procedure” that imitates a standard verification process. At the final stage, victims are asked to enter their seed phrase supposedly to complete the 2FA check. This is the moment when the wallet is compromised. The seed phrase is the master key to crypto assets. Anyone who gains access to it can restore the wallet on another device, sign transactions, transfer funds, and fully control the assets without the owner’s knowledge. Passwords, two-factor authentication, and device confirmations are irrelevant in this scenario.
Wallet providers consistently emphasize that a seed phrase should never, under any circumstances, be entered on websites, in forms, emails, or “security checks.” If a recovery phrase is requested anywhere, it is always a scam. This attack does not involve technical hacking. Instead, it relies on psychological pressure – urgency, fear of losing funds, the perceived authority of a “security service,” and familiar terminology.
Notably, despite the growing sophistication of such schemes, the total volume of losses from cryptocurrency phishing dropped significantly in 2025. According to analysts, losses fell by approximately 83% to around $84 million, compared with nearly $494 million the year before. However, this does not mean the problem has disappeared. On the contrary, attacks have become more targeted and depend heavily on market activity. The Scam Sniffer report notes that phishing functions as a probability driven by user activity: during periods of strong market movements and increased transaction volumes, the number of victims also rises. For example, in the third quarter of 2025, amid a powerful Ethereum rally, the highest phishing losses were recorded – about $31 million.

The MetaMask case once again highlights a fundamental principle of crypto security: no one ever has the legitimate right to ask for your seed phrase. Neither customer support, nor “2FA updates,” nor “mandatory security checks” require a recovery phrase. Any such request is a direct signal of fraud. In crypto, it is not the boldest who survive, but the most disciplined.
All content provided on this website (https://wildinwest.com/) -including attachments, links, or referenced materials — is for informative and entertainment purposes only and should not be considered as financial advice. Third-party materials remain the property of their respective owners.