🚨 Hackers targeted the JavaScript ecosystem: a massive crypto wallet swap ended with only $50 stolen.
One of the loudest incidents in the JavaScript ecosystem in recent years occurred: attackers managed to compromise a developer account on NPM — the largest package repository for JavaScript — and injected malicious code into several popular libraries. Millions of developers worldwide use these libraries, and total downloads have already exceeded billions.
By the way, you can buy legendary hardware wallets for beginners here, with all the basic features!
The malware’s goal was both simple and sophisticated: silently swap users’ cryptocurrency addresses “on the fly” during transactions so that funds would go directly to the hackers instead of the intended recipients.
However, the outcome was unexpected: according to Security Alliance, the total damage was only around $50 in ETH and meme coins. The sum may seem trivial compared to the scale of infection, but experts warn — the danger remains. Malici
How the attack happened
How the attack happened
Ledger’s CTO Charles Guillemet explained that this was a classic supply chain attack.
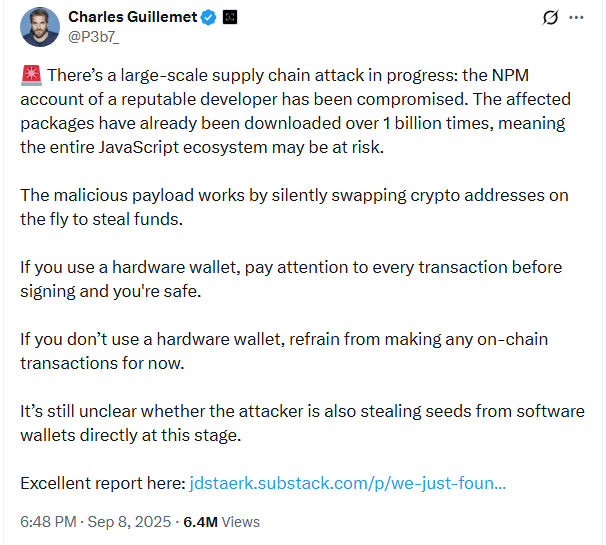
“A massive supply chain attack occurred: a reputable developer’s account on NPM was compromised. The affected packages have already been downloaded over a billion times, posing a threat to the entire JavaScript ecosystem.”
The compromised account belonged to well-known developer Josh Junon. Hackers conducted a phishing attack: an email supposedly from NPM support demanded that he urgently update two-factor authentication or face account suspension. By following the link, the developer effectively handed over access to the attackers.
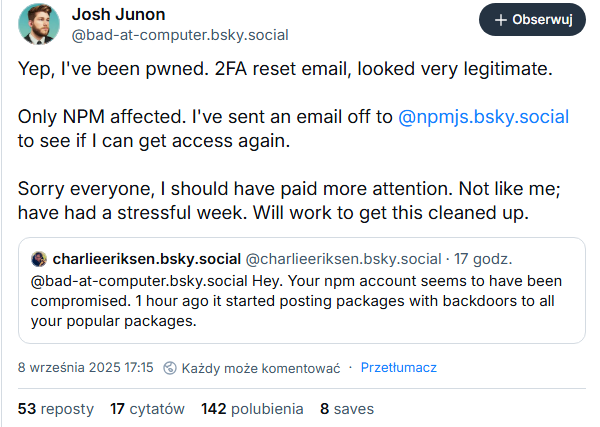
“The attacker embedded a malicious program into the code that searches for and steals cryptocurrency. The fetch function call, which broke our build, was the program’s attempt to send stolen data. The build failed only because the Node.js version was outdated and did not support fetch. In a more modern environment, the attack could have gone unnoticed.”
As a result, they gained access to popular packages, including the Chalk library, widely used in Node.js projects. Malicious code was embedded within complex and obfuscated functions, making detection difficult.
Developer JD explained that the first signs of the attack appeared as a failure in the CI/CD system. The team noticed “strange and deliberately obfuscated code,” including the fetch function call that broke the build due to the outdated Node.js version. Ironically, this incompatibility helped detect the issue faster: in a modern environment, the malware would have worked silently and gone unnoticed.
How the malware worked
According to experts, the malware operated in two modes:
- Passive mode: if a website did not detect a connected wallet, the code interfered with basic browser functions and swapped crypto addresses. To make the swap less noticeable, the Levenshtein algorithm was used to select addresses that closely resembled the original.
- Active mode: during a transaction, the malware intervened in the signing process and swapped the recipient address at the last moment. If the user did not manually verify the data, funds went to hackers.
The attack targeted major cryptocurrencies: BTC, ETH, SOL, TRX, LTC, and BCH.
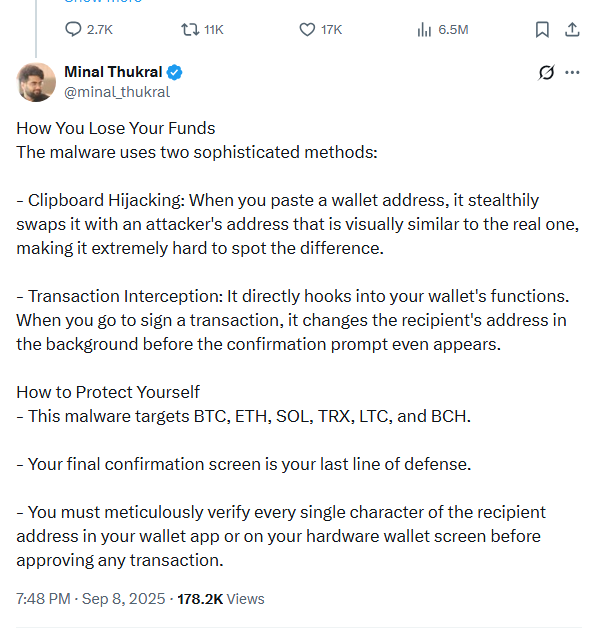
“The attack targets theft of BTC, ETH, SOL, TRX, LTC, and BCH. The final confirmation screen is your last line of defense. Carefully check every character of the recipient address in the app or on your hardware wallet screen before confirming any transaction,” said Okto ecosystem development head, Minal Tukral.
DeFi Llama founder, under the pseudonym 0xngmi, noted that wallets are not emptied automatically — the user still needs to approve the transaction. Therefore, the final confirmation screen in the app or on a hardware device remains the last line of defense.
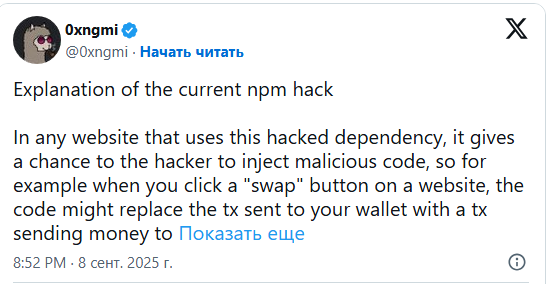
“A hacker can inject malicious code into any site using the compromised npm dependency. For example, when you click the ‘swap’ button, the malware could alter the transaction and send funds to the hacker. However, you will still see this suspicious operation in your wallet and must approve it — your funds will not disappear instantly.”
Who is at risk and how to protect yourself
According to Charles Guillemet, the highest risk is for software wallet users. Hardware wallet owners are safer because each action requires physical confirmation.
Okto ecosystem development head Minal Tukral emphasized: “Before confirming a transaction, carefully check the recipient address. Even one wrong number or character can result in loss of funds.”
Expert recommendations:
- carefully check transactions before confirming;
- use hardware wallets for storing significant amounts;
- avoid suspicious links, even if they appear official;
- update packages only from trusted sources and follow security news.
Community reaction
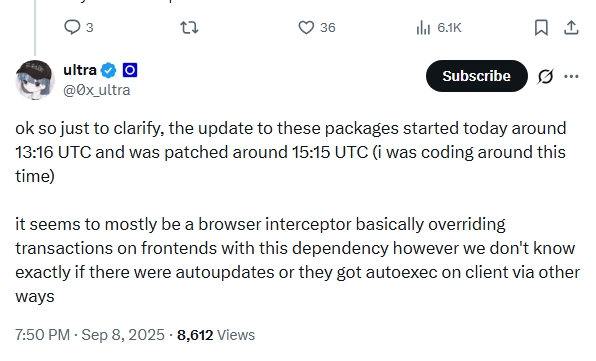
Developer ultra reported that the infected packages were fixed on September 8 at 15:15 UTC. Engineer cygaar confirmed that the NPM team disabled the compromised package versions.
Although the financial loss was “minimal,” the incident sparked serious discussion in the community: it demonstrated how vulnerable the global JavaScript ecosystem is to supply chain attacks. Compromising a single reputable account can threaten millions of projects and users.
Previously, ReversingLabs researchers had warned about similar methods: malicious code in NPM can use Ethereum smart contracts to hide commands and download viruses.
🕵️♂️ Conclusion
This time, hackers stole only $50, but the attack serves as a warning signal. Supply chain vulnerabilities are a time bomb, and each new incident increases the risk of global consequences.
By the way, you can buy legendary hardware wallets for beginners here, with all the basic features!
All content provided on this website (https://wildinwest.com/) -including attachments, links, or referenced materials — is for informative and entertainment purposes only and should not be considered as financial advice. Third-party materials remain the property of their respective owners.


